What exactly is ransomware?
If you’ve ever watched an action movie from the 90’s, there’s a good chance you may have heard the term ransom before. Except this time, the criminals haven’t kidnapped the main character’s daughter, they’ve taken over your website
If you aren’t familiar with the word ransom, it’s a sum of money or other payment demanded for the release of a prisoner.
Ransomware shares a similar concept, but instead of holding an individual hostage, criminals take control over your technology. More specifically—websites, file servers, or even entire devices.
These kinds of attacks aren’t anything new, in fact they’ve been around since the early days of the internet with the first recorded attack taking place in 1989. The concept is still the same, but since technology has evolved, so have the methods criminals can use to steal your money as estimate put the damages from ransomware attacks in 2021 around $20B.
Is ransomware malware?
Yes. In cases where ransomware is a serious threat, it’s the result of malicious software.
There are some situations where you can get spam emails that are pretending to be ransomware attackers. They’ll use intimidation to try and get victims to panic pay or to click on malicious links without them ever actually doing anything besides sending an email.
How is it installed?
In order for the extortion process to begin, the bad guys have to find a way to infect/infiltrate a device or server. There are a few techniques they can use to do so, most of which involve minimal actions required by the person on the receiving end of the attack.
Here are common methods in which ransomware can be installed
1. Spam emails/phishing links
By far the most common method used by cyber criminals is the use of emails to send out harmful links or attachments to the masses via phishing. These emails can either be extremely easy to spot or nearly identical to emails you would receive from a bank or your co-workers. The links/attachments can also appear to lead to official websites or look like PDF/Word documents
2. Social engineering
This is a complex tactic where the scam typically doesn’t start out with any immediate indicators of a threat. The goal of the bad guys here is to gain your trust using various methods such as trying to start a friendship/relationship or posing as your boss/owner of the company. While some social engineering attempts will only contain 1-2 emails, some scammers will send dozens of emails/messages over the course of several months until sending any malicious links.
3. Malicious pop-ups/advertising
This type is becoming less common than it used to be due to how web browsers and search have evolved but are still worth mentioning. If you ever see a random pop on a page you don’t typically visit that’s says “several viruses were detected on your device, click here to scan for threats”, clicking it could result in malware or remote access software installation that will wreak havoc on your device. The same concept applies to any ads on the sidebar that say anything along the lines of “click to receive money/free stuff”.
4. Social media links
Similar to phishing done though emails, criminals can use platforms such as Facebook, Twitter, etc. to get you to click on link they send through a messaging app. They may pretend to be a friend, or perhaps say you’ve won a random sweepstakes—either way, never click on any links unless you can be %110 sure you know the person who sent it actually sent it.
Types of malware
Once the ransomware is installed via whichever technique, a few things can happen depending on what kind of attack the criminals are employing.
1. Fake tech support/anti-virus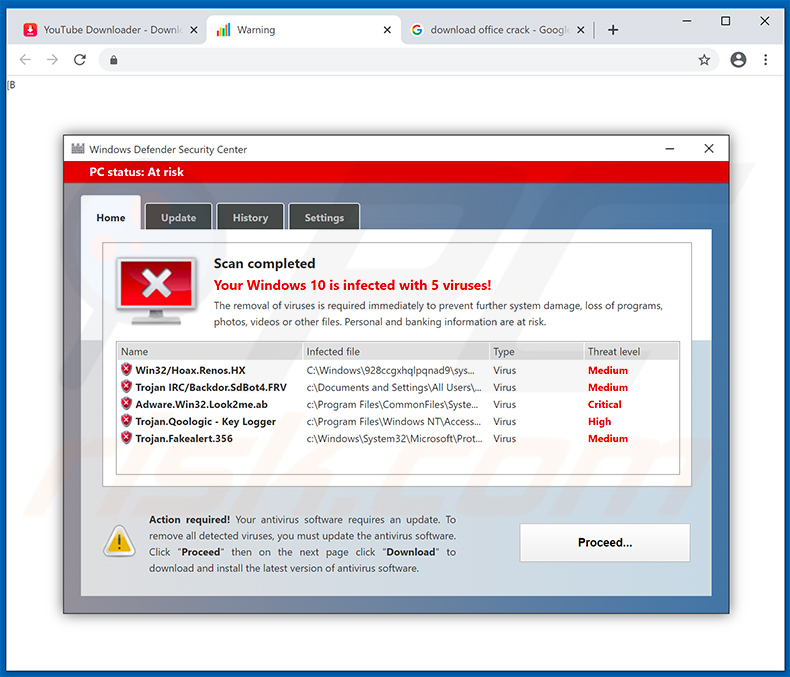
The least harmless type of ransomware, once installed, starts barraging you with anti-virus popups. These popups will ask for payment but will promise to remove all viruses and malware that have compromised your computer, when in reality the only threat is the popup itself. Your real anti-virus will never demand payment to remove threats, but this goes to show why it’s important to familiarize yourself with your current anti-virus pop ups.
2. Screen lock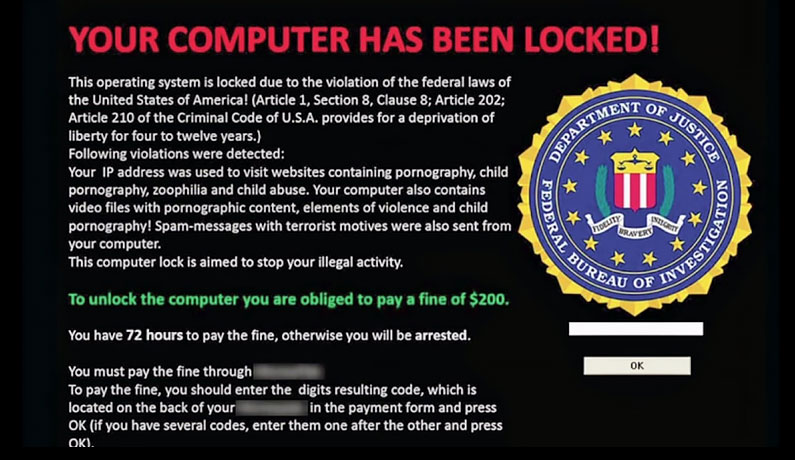
This form of ransomware behaves like you’d think based off the name. Criminals will completely lock you out of your device, leaving you stuck at a screen that’s demanding payment if you ever want to regain access again. The criminals may even pretend to be the FBI, with the lock-out screen stating that you’re under arrest because they found incriminating evidence on your computer.
3. Encryption
The most common and most serious type of malware attack is one centered around encrypting files located on a device or server. What makes this so dangerous is the fact that it’s nearly impossible to recover the information once it’s encrypted, depending on how complex the software the criminals use is. One scary thing to note is there’s a whole underground market for encryption-based ransomware where the most advanced cybercriminals are monetizing ransomware by offering ransomware-as-a-service programs.
What if I am a victim of ransomware?
It all depends on how you are affected, but it may come as a surprise that one of the best things you can do is NOT pay the ransom. According to the FBI, there is no guarantee that anything will happen even if you do pay the ransom, so you’re better off saving your money and losing your files rather than losing both.
Validate or eliminate
This concept can be applied to most, if not all scams that revolve around you clicking on a link or opening an attachment.
If you receive an email from a coworker/boss/friend and it contains a link or attachment, verify with the person who sent it, or with other coworkers to confirm it’s legitimacy. It may seem like a redundant thing to do, but all it takes is a quick, “hey, did you send me this?” to potentially save yourself or your company thousands of dollars. Keep in mind that all it takes is one simple click to compromise a whole system.
1. For the fake tech support/anti-virus
The best thing to try, would be running your actual anti-virus. Since this attack is malware, your anti-virus may detect it. If that doesn’t work, it’s worth taking it to a trusted professional to clean up the device. While fake pop-ups may be one aspect of ransomware, there could be several other hidden pieces that have gone undetected.
2. For screen lockouts
Firstly, disconnect your device from the internet. Then, as with the fake tech/support, take the computer to an IT professional. They may or may not be able to regain access, it all relies on the sophistication of the software.
3. For Encrypted files
If a criminal is using an advanced enough program, there may not be much you can do in terms of recovery. If it isn’t an up-to-date program, there are some options to install decryption software that may allow you to recover some data back.
Overall, the best thing to do for ransomware is to avoid it in the first place. This is obviously a lot easier said than done, but it demonstrates how knowing what to look for and what not to click is the best form of defense against these kinds of threats.



